- Home
- Information Technology
-
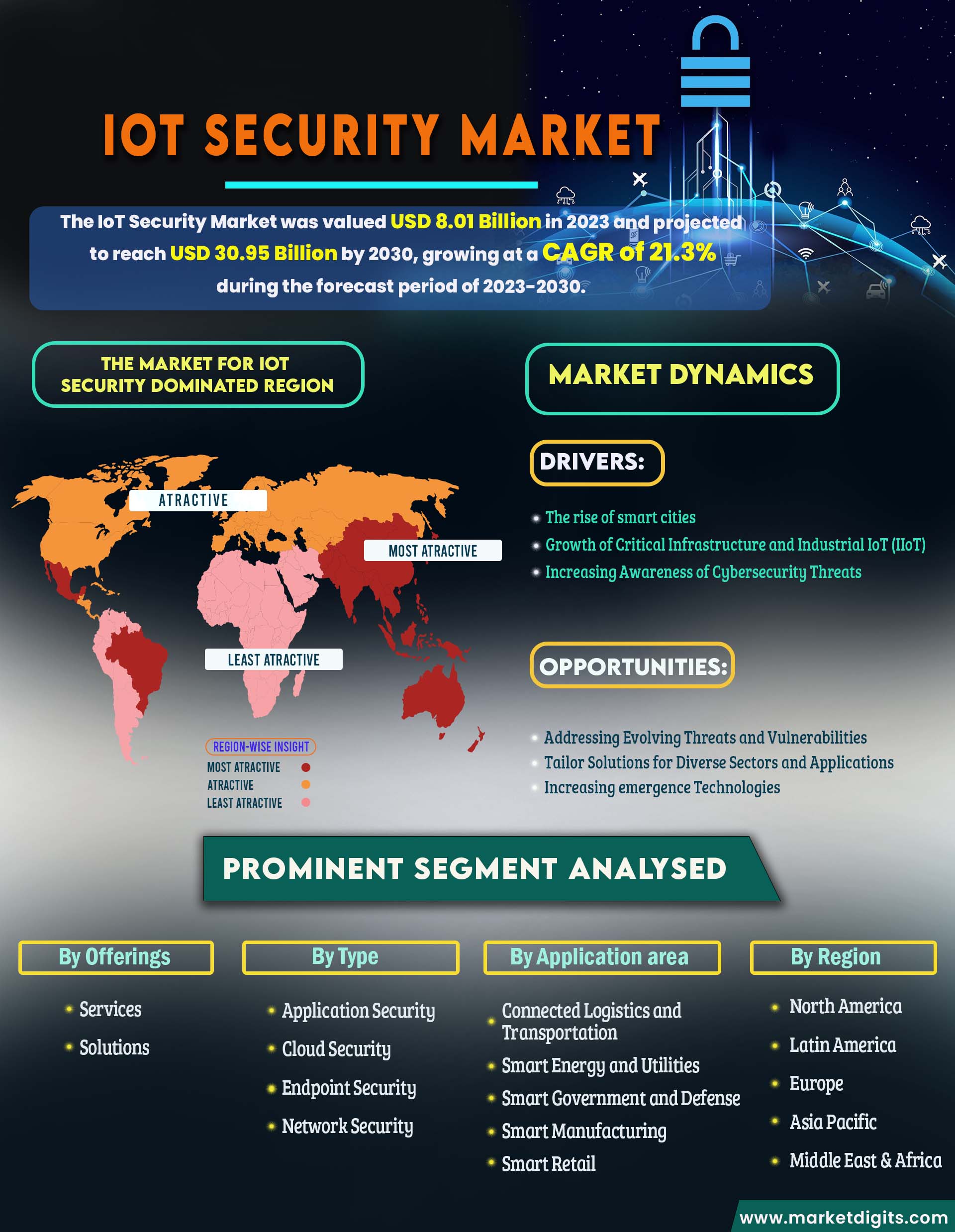
IoT Security Market

IoT Security Market By Offerings (Services, Solutions), Solutions, Services (Managed Services, Professional Service), Professional Services ,Type, Application area, Data Sensitivity and Region - Partner & Customer Ecosystem (Product Services, Proposition & Key Features) Competitive Index & Regional Footprints by MarketDigits - Forecast 2024-2032
Industry : Information Technology | Pages : 149 Pages | Published On : May 2024
Market Overview
The IoT security market is experiencing robust growth driven by the increasing adoption of Internet of Things (IoT) devices across various industries. As the number of connected devices continues to soar, concerns about cybersecurity threats and vulnerabilities have escalated, propelling the demand for advanced security solutions. Organizations are investing heavily in IoT security to safeguard sensitive data, prevent unauthorized access, and mitigate potential cyber risks. The market is characterized by a proliferation of innovative technologies such as blockchain, artificial intelligence, and machine learning, aimed at fortifying the resilience of IoT ecosystems. Additionally, stringent regulatory frameworks and compliance requirements are compelling businesses to prioritize IoT security solutions, further fueling market expansion. With a growing awareness of the critical importance of securing IoT infrastructures, the IoT security market is poised for sustained growth as companies seek comprehensive, adaptive security measures to protect their interconnected environments.
Major vendors in the global IoT Security Market: Broadcom Inc. (Symantec Corporation), IBM Corporation, Check Point Software Technologies Ltd., Intel Corporation, Hewlett Packard Enterprise Co., Cisco Systems Inc., Fortinet Inc., Trustwave Holdings, Thales Group (Gemalto NV), AT&T Inc., Palo Alto Networks Inc and Others
The frequency of data breaches is on the rise
The escalating frequency of data breaches has emerged as a compelling driver for the IoT Security Market. As the number of interconnected devices in the Internet of Things (IoT) ecosystem continues to surge, the attack surface for cyber threats expands exponentially. The increasing sophistication of cyberattacks and the potential compromise of sensitive data have heightened awareness among businesses and individuals regarding the critical need for robust IoT security measures. Organizations across various industries are recognizing the imperative of safeguarding their IoT infrastructures against unauthorized access, data breaches, and other cybersecurity risks. This heightened awareness, fueled by the rising incidence of data breaches, is propelling significant investments in IoT security solutions, driving the market's growth as stakeholders prioritize comprehensive measures to ensure the integrity and resilience of their interconnected environments.
Market Dynamics
Drivers:
- The rise of smart cities
- Growth of Critical Infrastructure and Industrial IoT (IIoT)
- Increasing Awareness of Cybersecurity Threats
Opportunities:
- Addressing Evolving Threats and Vulnerabilities
- Tailor Solutions for Diverse Sectors and Applications
- Increasing emergence Technologies
Convergence of IT and OT Security
The trend towards the convergence of Information Technology (IT) and Operational Technology (OT) security is a notable development in the IoT Security Market. Traditionally, IT and OT operated in silos, but the increasing integration of IoT devices has blurred the lines between these domains. As industries leverage IoT for operational efficiency, the need to align IT and OT security strategies has become paramount. The convergence allows for a holistic approach to security, addressing vulnerabilities across both IT and OT networks. This integration is driven by the recognition that a unified security framework is essential to protect against cyber threats that can exploit the interconnectedness of IT and OT systems. As organizations strive for a cohesive security posture, the convergence trend is shaping the landscape of IoT security solutions, promoting comprehensive measures that bridge the gap between traditionally distinct realms of technology.
Asia-Pacific dominates the market for IoT Security Market.
The Asia-Pacific region stands out as a key hub for IoT adoption, primarily driven by the implementation of smart city initiatives. The substantial industrialization and a growing number of mobile device users in the region indicate a significant anticipated expansion. According to the Cisco VNI report, projections for 2022 suggest that the region might witness a surge to 2.6 billion internet users, constituting 62% of the population, compared to 1.7 billion (41% of the population) in 2017. Additionally, the region is expected to host 13.1 billion networked devices/connections by 2022, up from 8.6 billion in 2017. However, Asia-Pacific faces a 35% higher likelihood of being targeted by advanced cyber-attacks, as reported by FireEye. The National Institute of Information and Communication Technology (NIICT) notes a significant uptick in cyberattacks on IoT devices, projecting a potential increase to 30 billion devices by 2020, compared to 15 billion devices in 2015. In response to these challenges, governments and related organizations are increasingly deploying IoT security solutions to mitigate potential damages. China, with its technological innovation, notably influences the rise of IoT, fostering heightened demand in the smart home market among Chinese consumers, encompassing central systems for lighting control, security, entertainment, home appliances, and more.
Network Security Segments is anticipated to hold the Largest Market Share during the Forecast Period
Based on the type segment categorized into Network Security, Endpoint Security, Application Security, Cloud Security and Others. Network Security has a major share in the IoT Security Market. Enterprises globally identify IoT networks as primary targets and a top concern, with the network security segment encompassing various subsegments like firewalls, servers, VPN, IDS, IPS, WIDPS, gateway, and network hardware. The escalating adoption of Bring Your Own Device (BYOD) and IoT in enterprises amplifies security apprehensions regarding network attacks. Notably, the global network hardware market reached USD 181 billion in fiscal 2018, with enterprise network hardware alone valued at USD 52 billion, according to IT Candor. IBM X-Force threat intelligence reported a staggering 5,400% increase in IoT vulnerabilities in 2018 compared to five years prior, exemplified by the impactful Mirai attack in 2016, utilizing over 150,000 devices for a massive 1TB per second data assault on servers. Predominantly, IoT-based attacks manifest in Distributed Denial of Service (DDoS) form, with Symantec's report attributing nearly 80% of 2018's IoT attacks to three DDoS-associated malware: LightAidra, Kaiten, and Mirai. Market vendors are responding with specialized solutions to address network security challenges, exemplified by Palo Alto Networks' integration of IoT security into its firewall services following the acquisition of Zingbox, showcasing a broader industry trend to mitigate network threats and stimulate demand in the network
Major Segmentations Are Distributed as follows:
- By Offerings
- Services
- Solutions
- By Solutions
- Data Encryption and Tokenization
- Device Authentication And Management
- Distributed Denial Of Service Protection
- Identity and Access Management
- Security Analytics
- Others
- By Services
- Managed Services
- Professional Service
- By Professional Services
- Consulting
- Implementation
- Support and Maintenance
- By Type
- Application Security
- Cloud Security
- Endpoint Security
- Network Security
- Others
- By Application area
- Connected Logistics and Transportation
- Smart Energy and Utilities
- Smart Government and Defense
- Smart Manufacturing
- Smart Retail
- Others
- By Data Sensitivity
- High-Sensitive Data
- Low and Moderate Sensitive Data
- By Region
- North America
- US
- Canada
- Latin America
- Brazil
- Mexico
- Argentina
- Colombia
- Chile
- Peru
- Rest of Latin America
- Europe
- UK
- Germany
- France
- Italy
- Spain
- Russia
- BENELUX
- CIS & Russia
- Nordics
- Austria
- Poland
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Thailand
- Indonesia
- Malaysia
- Vietnam
- Australia & New Zealand
- Rest of Asia Pacific
- Middle East & Africa
- Saudi Arabia
- UAE
- South Africa
- Nigeria
- Egypt
- Israel
- Turkey
- Rest of Middle East & Africa
- North America
Recent Developments
- May 2023, AWS introduces support for Transport Layer Security (TLS) 1.3 via Configurable Endpoints, enhancing security and performance by eliminating legacy features and cipher suites from previous TLS versions and streamlining the handshake process for improved efficiency.
- April 2023, IBM unveils IBM Security QRadar for IoT, a cutting-edge IoT security platform. The QRadar Suite integrates advanced AI and automation into a unified user interface, enhancing security analysts' efficiency and response speed throughout the entire attack chain.
IoT Security Market Report Gives Answers to Following Key Questions:
- What will be the IoT Security Market’s Trends & growth rate? What analysis has been done of the prices, sales, and volume of the top producers of IoT Security Market?
- What are the main forces behind the worldwide IoT Security Market? Which companies dominate the IoT Security Market?
- Which companies dominate the IoT Security Market? Which business possibilities, dangers, and tactics did they embrace in the market?
- What are the global Natural Food Colors industry's suppliers' opportunities and dangers in IoT Security Market?
- What is the Natural Food Colors industry's regional sales, income, and pricing analysis? In the IoT Security Market, who are the distributors, traders, and resellers?
- What are the main geographic areas for various trades that are anticipated to have astounding expansion over the IoT Security Market?
- What are the main geographical areas for various industries that are anticipated to observe an astounding expansion in IoT Security Market?
- What are the dominant revenue-generating regions for IoT Security Market, as well as regional growth trends?
- By the end of the forecast period, what will the market size and growth rate be?
- What are the main IoT Security Market trends that are influencing the market's expansion?
- Which key product categories dominate the IoT Security Market? What are the IoT Security Market’s main applications?
- In the coming years, which IoT Security Market technology will dominate the market?
Reason to purchase this IoT Security Market Report:
- Determine prospective investment areas based on a detailed trend analysis of the global IoT Security Market over the next years.
- Gain an in-depth understanding of the underlying factors driving demand for different xxx Market segments in the top spending countries across the world and identify the opportunities each offers.
- Strengthen your understanding of the market in terms of demand drivers, industry trends, and the latest technological developments, among others.
- Identify the major channels that are driving the global IoT Security Market , providing a clear picture of future opportunities that can be tapped, resulting in revenue expansion.
- Channelize resources by focusing on the ongoing programs that are being undertaken by the different countries within the global IoT Security Market.
- Make correct business decisions based on a thorough analysis of the total competitive landscape of the sector with detailed profiles of the top IoT Security Market providers worldwide, including information about their products, alliances, recent contract wins, and financial analysis wherever available.
Cloud Engineering Market Size, Share & Trends Analysis, By Deployment (Public, Private, Hybrid), By Service (IaaS, PaaS, SaaS), By Workload, By Enterprise Size By End-use, By Region, And Segment Forecasts
TOC
Table and Figures
Methodology:
At MarketDigits, we take immense pride in our 360° Research Methodology, which serves as the cornerstone of our research process. It represents a rigorous and comprehensive approach that goes beyond traditional methods to provide a holistic understanding of industry dynamics.
This methodology is built upon the integration of all seven research methodologies developed by MarketDigits, a renowned global research and consulting firm. By leveraging the collective strength of these methodologies, we are able to deliver a 360° view of the challenges, trends, and issues impacting your industry.
The first step of our 360° Research Methodology™ involves conducting extensive primary research, which involves gathering first-hand information through interviews, surveys, and interactions with industry experts, key stakeholders, and market participants. This approach enables us to gather valuable insights and perspectives directly from the source.
Secondary research is another crucial component of our methodology. It involves a deep dive into various data sources, including industry reports, market databases, scholarly articles, and regulatory documents. This helps us gather a wide range of information, validate findings, and provide a comprehensive understanding of the industry landscape.
Furthermore, our methodology incorporates technology-based research techniques, such as data mining, text analytics, and predictive modelling, to uncover hidden patterns, correlations, and trends within the data. This data-driven approach enhances the accuracy and reliability of our analysis, enabling us to make informed and actionable recommendations.
In addition, our analysts bring their industry expertise and domain knowledge to bear on the research process. Their deep understanding of market dynamics, emerging trends, and future prospects allows for insightful interpretation of the data and identification of strategic opportunities.
To ensure the highest level of quality and reliability, our research process undergoes rigorous validation and verification. This includes cross-referencing and triangulation of data from multiple sources, as well as peer reviews and expert consultations.
The result of our 360° Research Methodology is a comprehensive and robust research report that empowers you to make well-informed business decisions. It provides a panoramic view of the industry landscape, helping you navigate challenges, seize opportunities, and stay ahead of the competition.
In summary, our 360° Research Methodology is designed to provide you with a deep understanding of your industry by integrating various research techniques, industry expertise, and data-driven analysis. It ensures that every business decision you make is based on a well-triangulated and comprehensive research experience.
• Product Planning Strategy
• New Product Stratergy
• Expanded Research Scope
• Comprehensive Research
• Strategic Consulting
• Provocative and pragmatic
• Accelerate Revenue & Growth
• Evaluate the competitive landscape
• Optimize your partner network
• Analyzing industries
• Mapping trends
• Strategizing growth
• Implementing plans
Covered Key Topics
Growth Opportunities
Market Growth Drivers
Leading Market Players
Company Market Share
Market Size and Growth Rate
Market Trend and Technological
Research Assistance
We will be happy to help you find what you need. Please call us or write to us:
+1 510-730-3200 (USA Number)
Email: sales@marketdigits.com